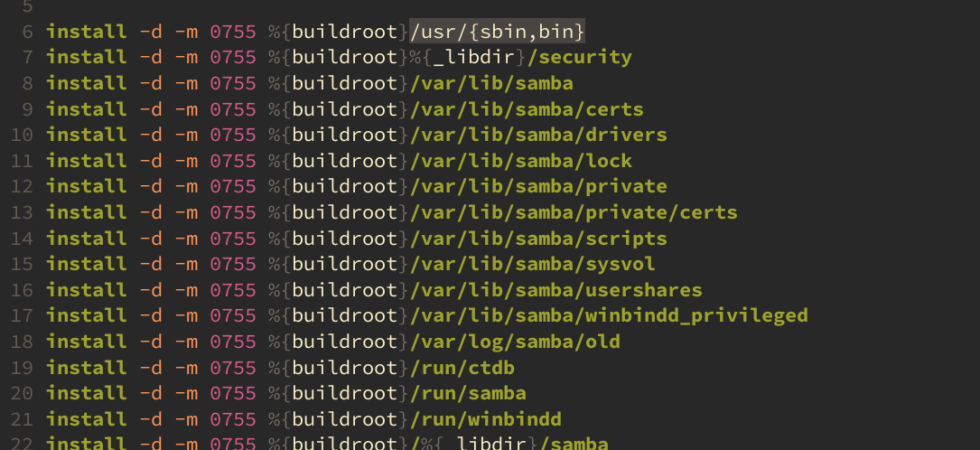
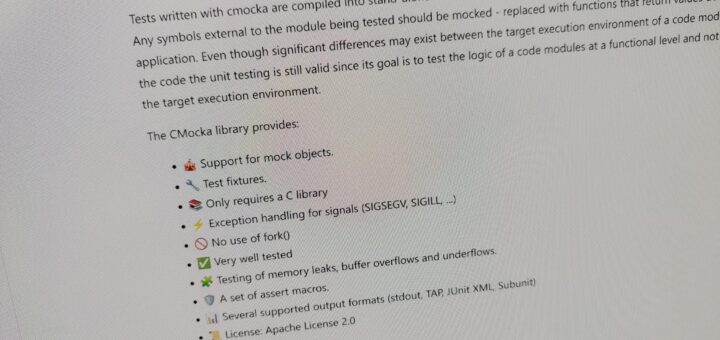
Some 🌳💞 for RPM Spec
Two years ago, I started to look into writing a tree-sitter parser as part of the “Day of Learning” at my employer. As I write and edit many RPM Spec files (also at work), I wanted better highlighting in my text editor, which is Neovim. I had attempted to start the project the year before but was lost. The next year, the tree-sitter documentation improved,...