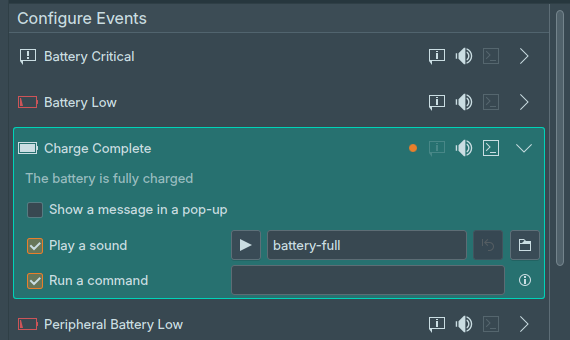
KDE: “Run a command” on notification trigger
KDE had a feature a lot of people didn’t know about. You could run a command when a notification triggered. The feature wasn’t very well documented and nobody really blogged about it. However with the release of KDE Plasma 6, the feature was removed. I learned about it by accident, as it is tracked by Bug #481069. I really need the feature and I re-implemented...